Today, people operate in two worlds — the physical and the digital. That is, we have material objects and their digital representations. For example, we have both physical and digital works of art, luxury goods, and documents (passports, driving licenses, etc.). One of the problems we face in combining these two worlds is the inability to securely and transparently connect physical objects to their digital counterparts.
When we have an item in the physical world and an associated item in the digital world, we want them to be tied to each other and verify each other’s authenticity. That is, we want a particular physical object to contain information about a related virtual object and vice versa.
Product authentication: current solutions
QR codes
A QR code is a type of matrix barcode: a machine-readable label that can contain URL to information about the item to which it is attached.

Let’s see how this might work with perfume bottles. Say there are authentic and knockoff perfumes, the only difference being a QR code on the authentic perfume bottles. This QR code redirects to a site that confirms the perfume bottle’s authenticity.
The disadvantage of this system is that anyone can scan the QR code, print a copy, stick it on any perfume bottle, and sell it as authentic. The QR code sends a user to a link to learn more about the product, but it doesn’t guarantee the product’s authenticity.
For example, producers can apply QR codes to bottles of expensive wine, and customers can scan these codes using an application that verifies a bottle’s authenticity based on records in a blockchain. The disadvantage of this verification method is that this code can be copied and pasted onto another bottle of wine, or even onto a bottle of water, and no one will be able to prove that it’s a fake.
Read more about Blockchain development services.
NFC tags
NFC tags are more complex. An NFC tag initiates some action on a smartphone when the phone is within close proximity. The user can be redirected to a website, or an application or popup can open.

NFC tags contain an induction coil and a small chip. They work by reading and encrypting information. Anyone can read an NFC tag, and they are cheap (from $0.07 a piece) and easy to record in bulk.

This is a more complex verification method than a QR code. Some advanced versions of NFC tags even allow for storing encrypted or randomly generated keys, but this still does not solve the product authentication problem.
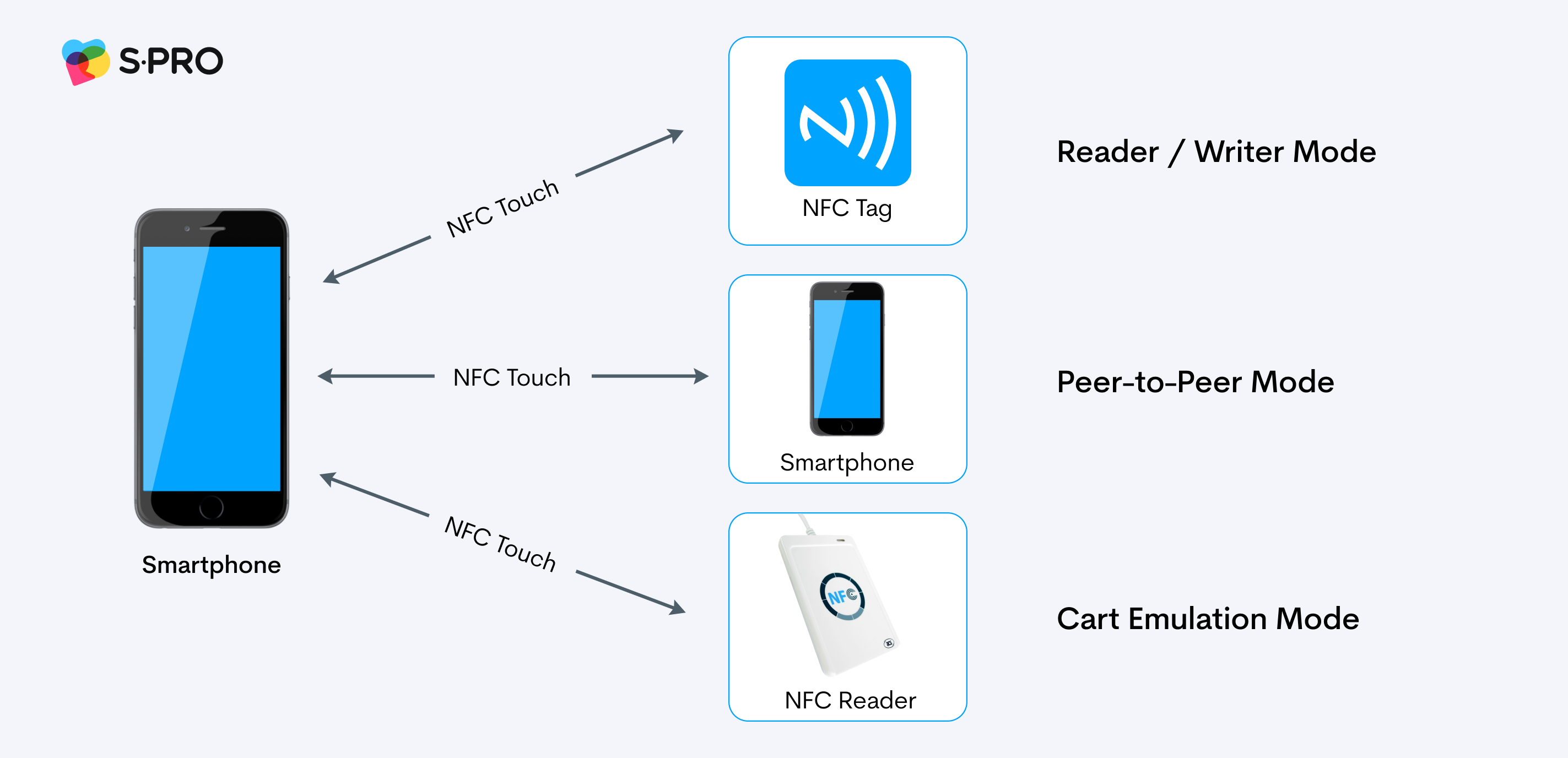
The disadvantage of NFC authentication is that even reliably encrypted and secure tags with random keys can still easily be read and duplicated. And if this happens, it’s impossible to distinguish a fake product from the original.
S-PRO authentication technology – Bidirectional NFC
There is a third method that overcomes all of the above disadvantages: a hardware solution with a chip that doesn’t require power. These chips allow you to connect virtual and physical products as securely as possible. At S-PRO, we can create a complete ecosystem for you to work with these chips.
S-PRO can work with you to design a hardware prototype, product specification, and libraries for integrating the hardware into your product. This could be a product created by us, or it could be a product created by your own developers, in which case you will need to integrate the hardware solution yourself.
With our minimum service package, you’ll get the eight items described below. However, we can provide even more services and build whatever you wish according to your needs.
Stage 1 – Prototype
- Working prototype
- Hardware specification
- Integration requirements
- A rough estimate of manufacturing cost at scale
Stage 2 — Integration (so chips can interact with other systems within your ecosystem)
- Libraries and a set of instructions
- Integration team onboarding
- Integration documentation
- Estimation support
As a result, you will get the following:
- Several working chip hardware units
- A production map showing how to produce the chips, where to order them, what they should consist of (processor, coil, how it should be stitched), and the method of flashing the chips
- An admin panel where all the chips will be stored, along with their unique secret keys
- General instructions on how to implement the chips in your product
Bidirectional NFC is a complex, innovative, reliable, and secure product verification solution to verify any physical or digital product. We are ready to discuss all its nuances and advantages with you.





